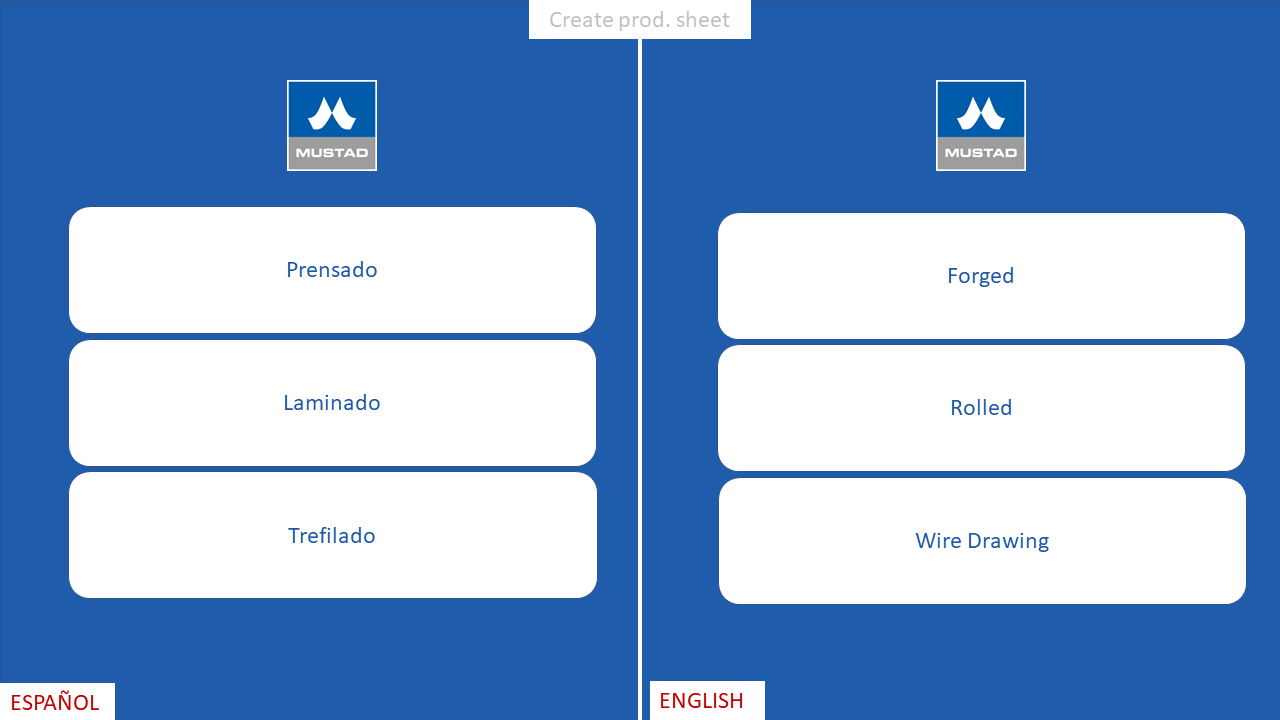
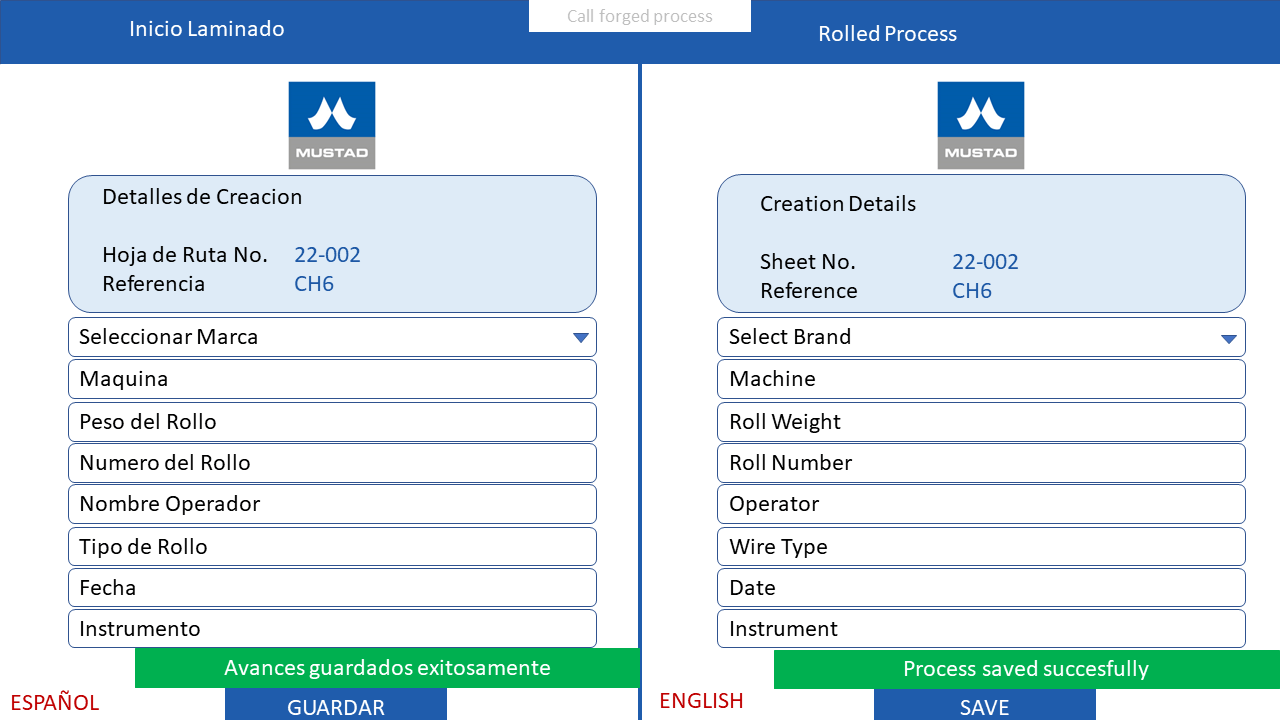
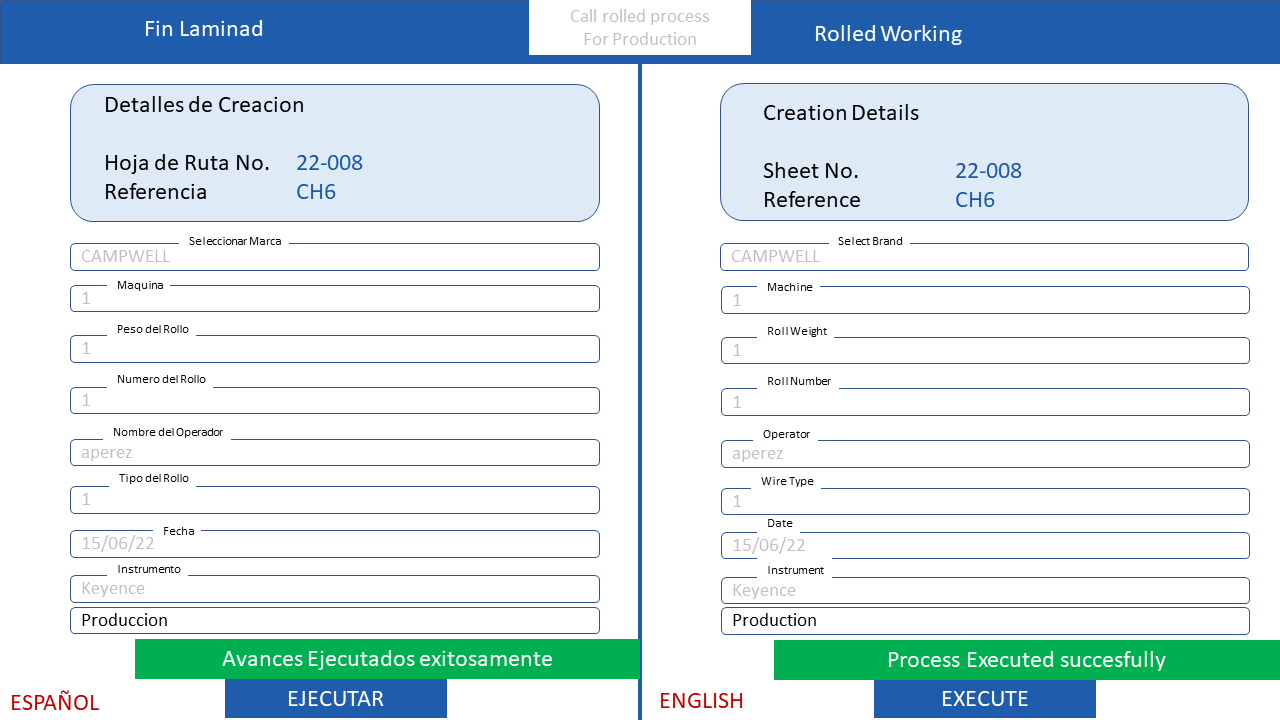
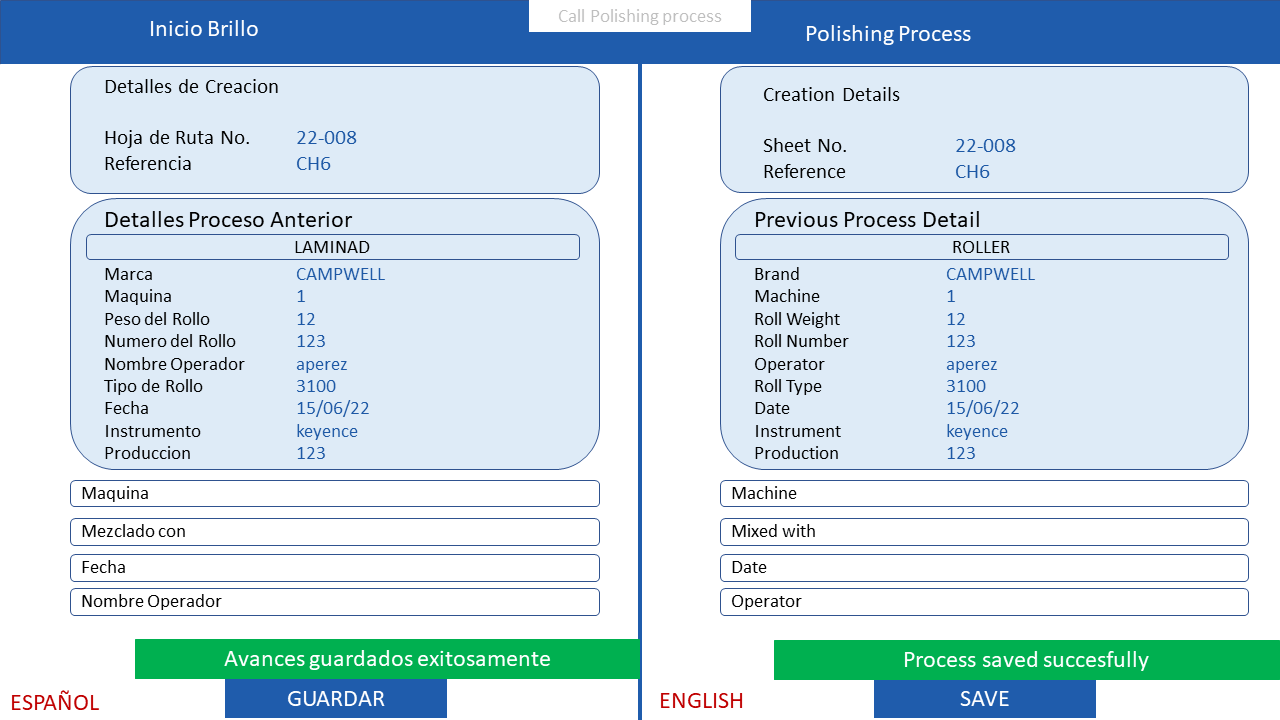
ICAM




Challenge
The United States has experienced a number of extreme events in recent years, including record-breaking fires, natural disasters, mass shootings, and a major global pandemic. These events have strained the resources of local jurisdictions, requiring them to coordinate and seek assistance from other agencies, jurisdictions, and disciplines.
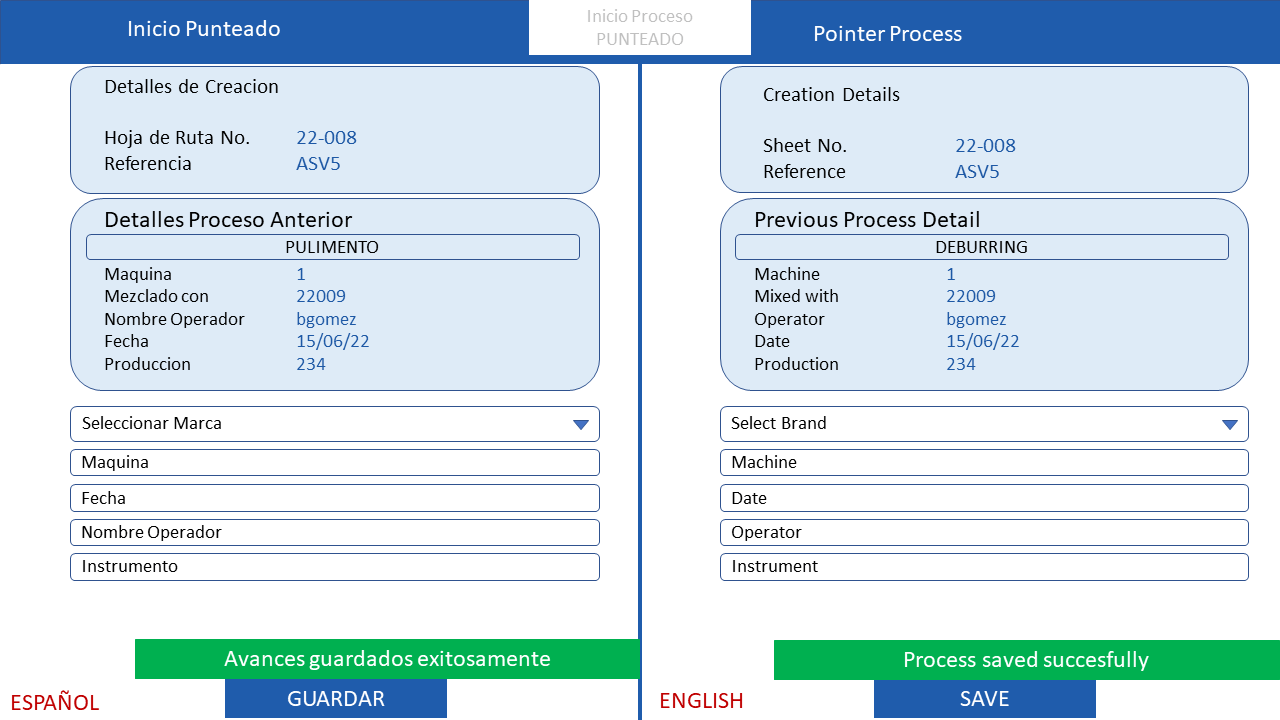
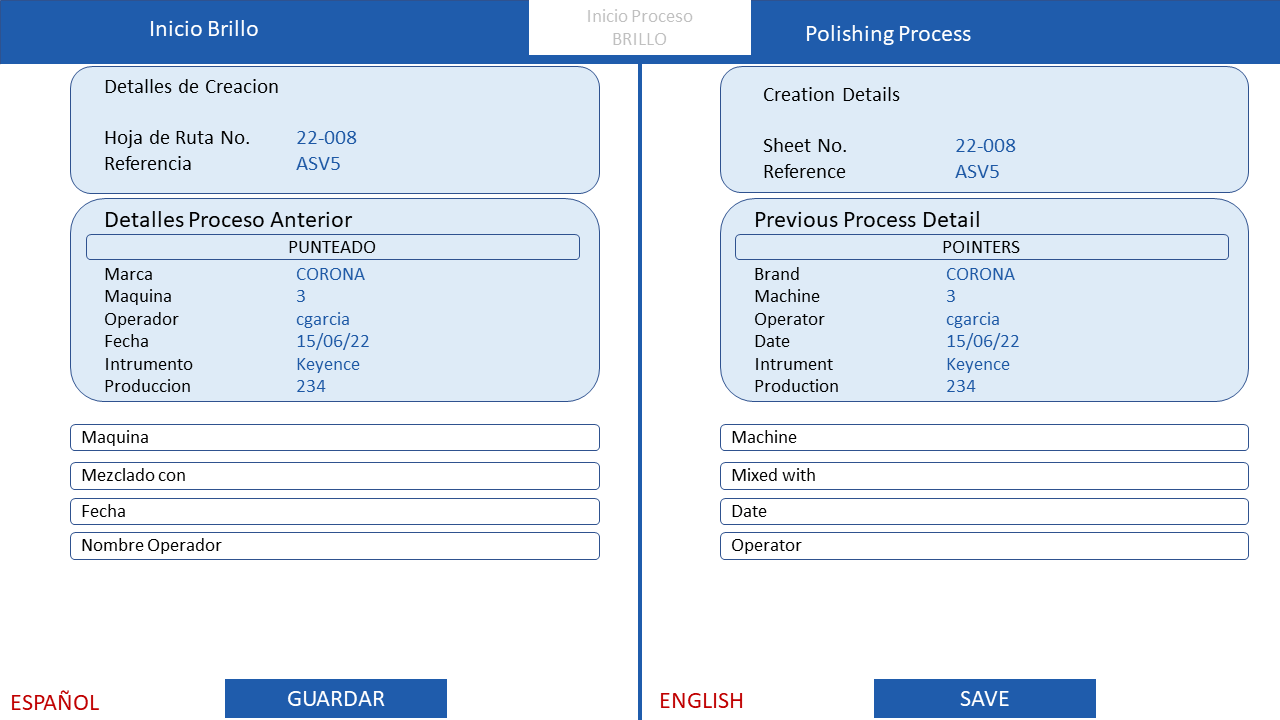
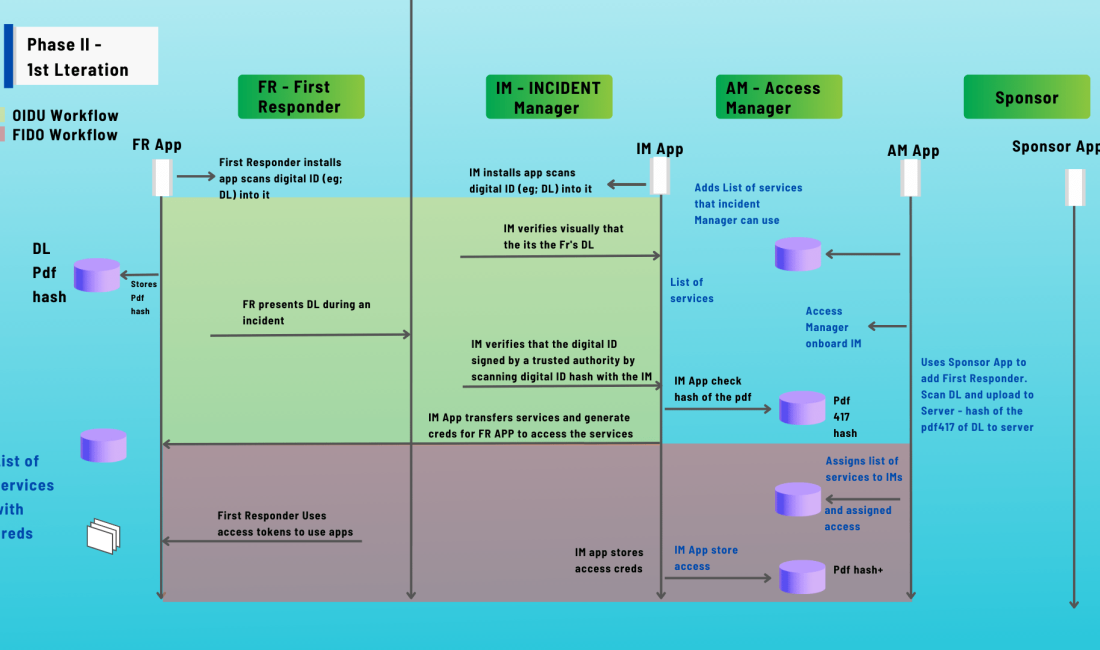
Incident Commanders (ICs) play a critical role in coordinating these efforts. They need to be able to quickly and easily identify and secure the personnel with the right credentials from multiple areas. They also need to be able to coordinate cooperation between First Responder communities and establish a consent-related trust mechanism.
There are a number of organizations that can benefit from secure credentials for ICs. These include:
- First Responders
- Public Safety and Security Communities
- Federal agencies
- Interoperable efficiencies between federal agencies through the Trustmark framework
In order to secure credentials for ICs, there are a number of challenges that need to be addressed, such as identity management, access control, and data protection. There are a number of solutions that can be used to address these challenges, such as identity and access management (IAM) solutions, zero trust architecture, and data protection solutions.
By addressing the challenges and implementing the solutions that are available, ICs can help to ensure that they have the secure credentials that they need to respond to extreme events.
Solution Delivered
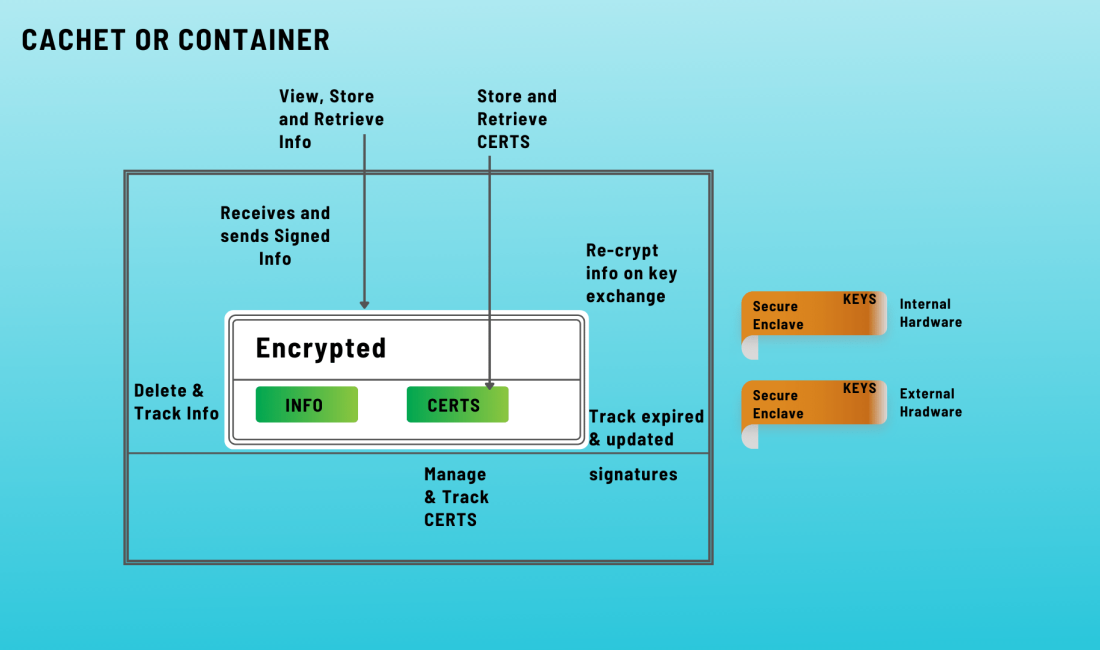
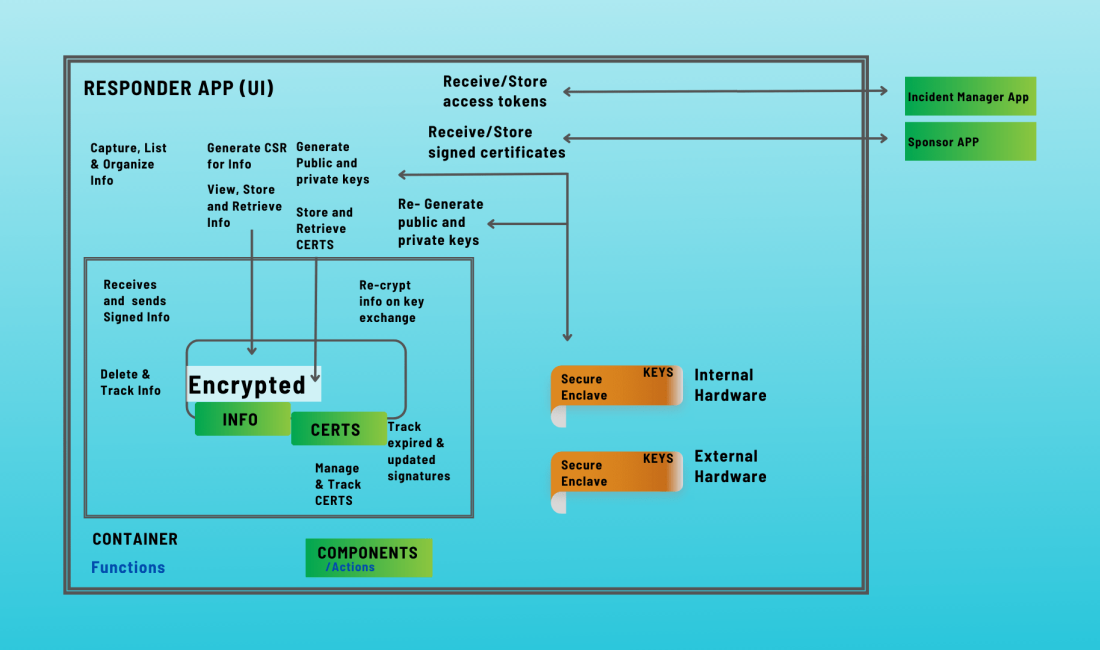
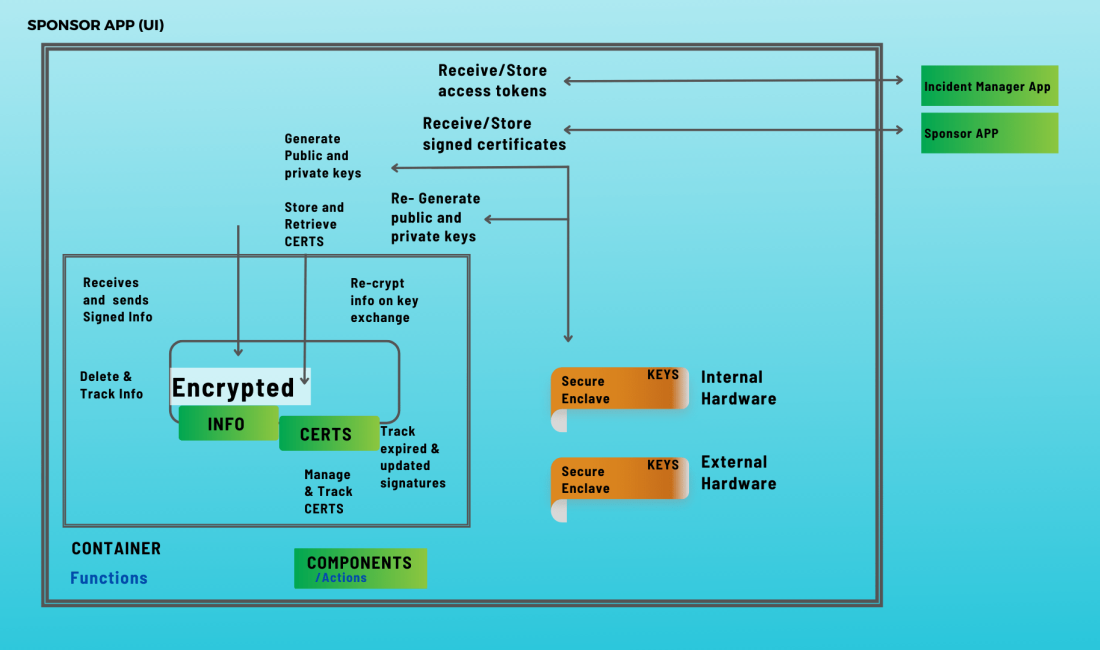
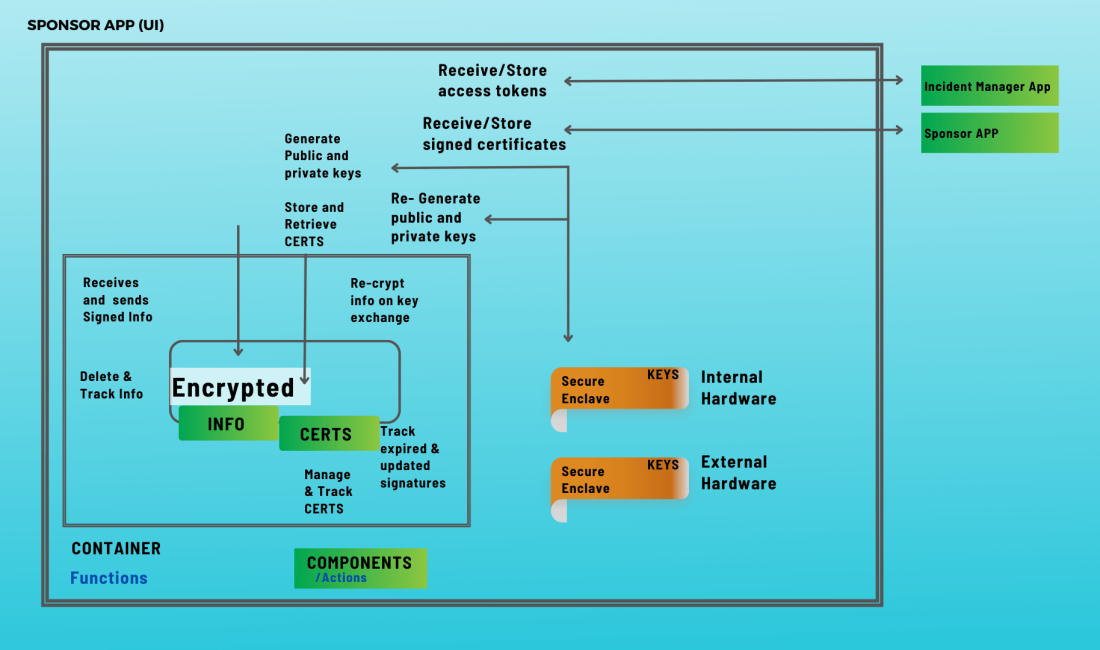
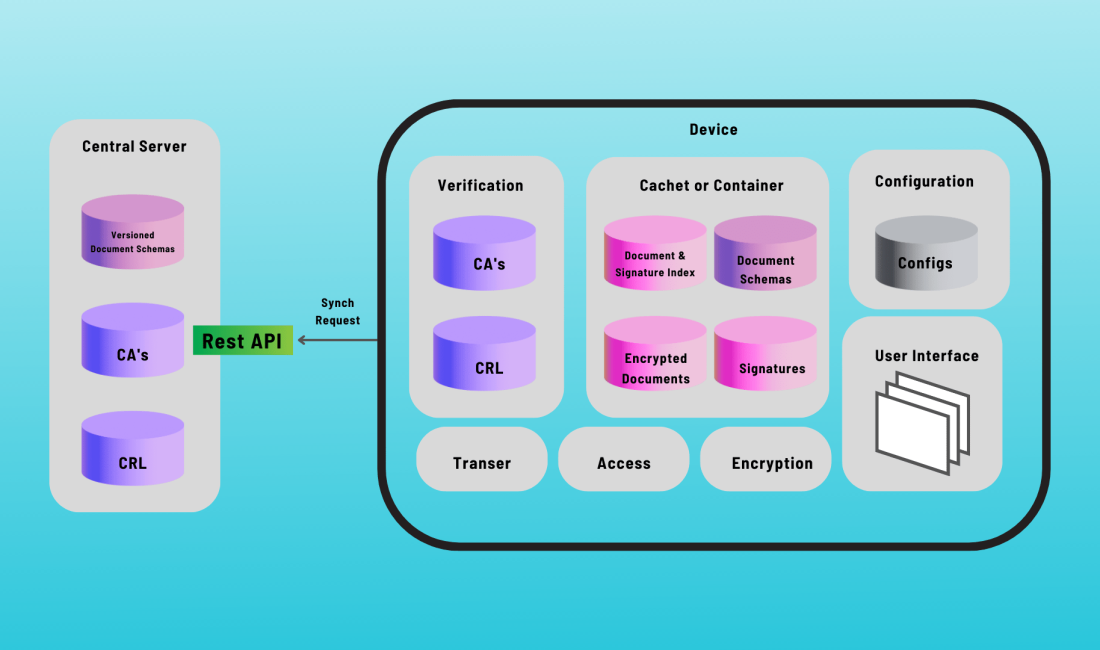


IMPact
Secureflo.dev offers a cost-effective and secure solution to stabilize incident activities, enhance interoperable communications, safeguard privacy for public safety personnel, reduce identity fraud and hacking, and proactively mitigate cyberattacks and network intrusions. Benefits to the Customer:
- Accelerated and improved incident stabilization.
- Enhanced effectiveness of emergency responders and first responders.
- Validated identification of first responders from different areas and organizations.
- Secure protection, sharing, and maintenance of records.
ICAM



Technologies